How to Manage Roles
About 696 wordsAbout 2 min
I. Function Introduction
Role management is the core module of enterprise permission systems, with main functions including:
- Permission Assignment: Achieve fine-grained permission control through roles
- Organizational Collaboration: Define responsibility boundaries for different positions
- Security Management: Ensure secure and compliant data access
- Efficiency Improvement: Configure user permissions in batches
Access Entry:
- Log in to Management Backend
- Navigation menu select: 【System Settings】→【Roles】
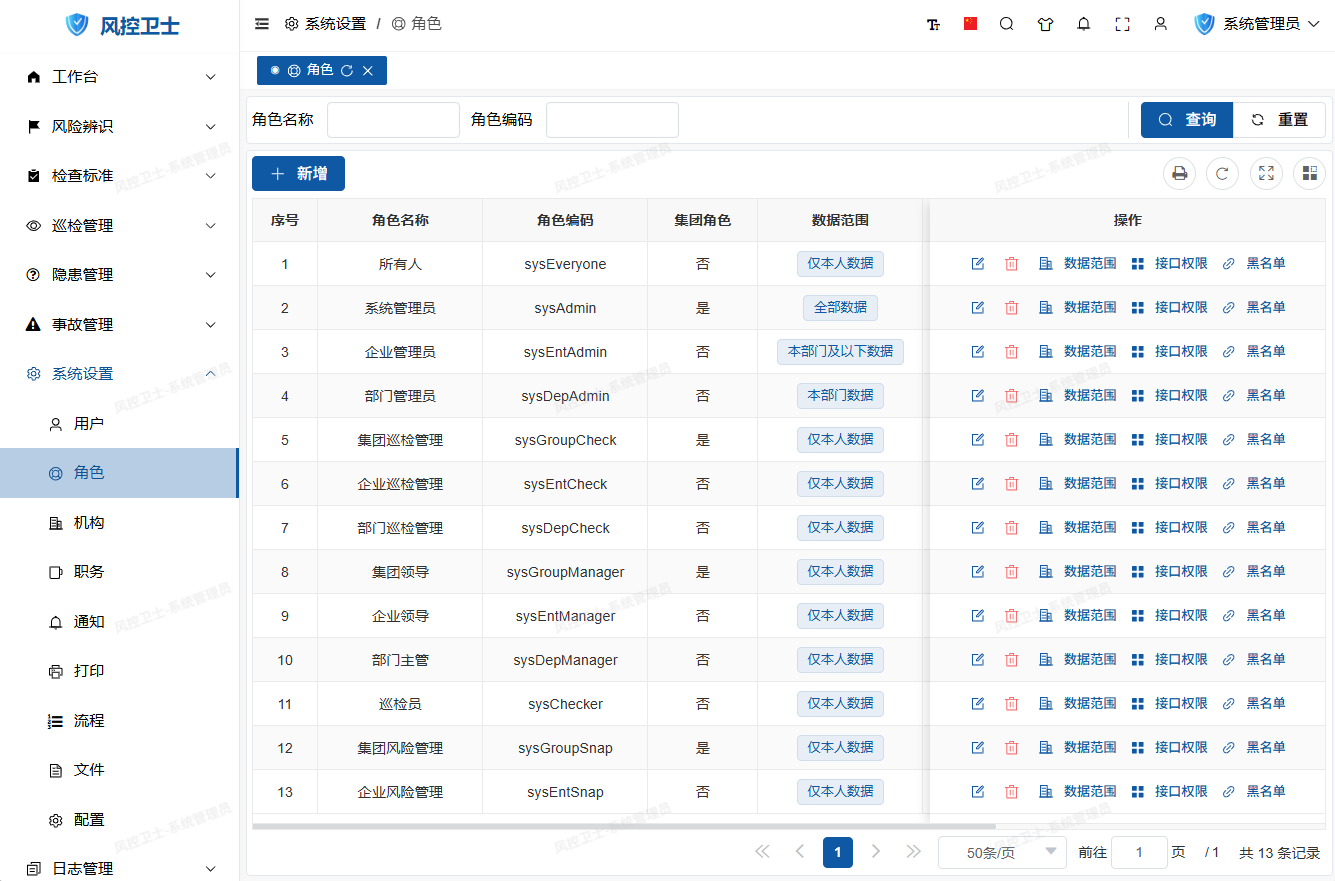
II. Operation Guide
1. Add New Role
Operation Steps:
- Click "New" button on toolbar
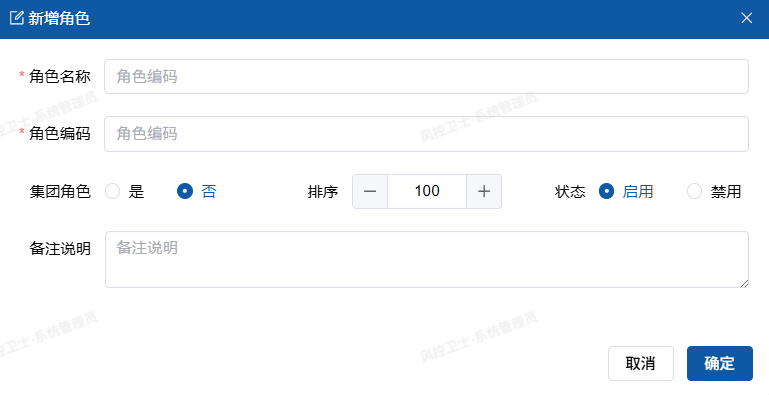
- Fill in basic information:
- Role Name (Required, e.g. "Finance Specialist")
- Role Code (Unique identifier, recommended English abbreviation)
- Role Description (Function description)
- Click "Confirm" to save
2. Modify Role
Operation Steps:
- Locate target role
- Click "Edit" button in operation column
- Modify information:
- Basic information (name/code)
- Status (Enable/Disable)
- Sorting weight
- Click "Confirm" to save
3. Delete Role
Operation Steps:
- Select target role
- Click "Delete" button in operation column
- Confirm deletion
Precautions:
- Roles assigned to users cannot be deleted
- System initial roles cannot be deleted
4. Configure Interface Permissions
Operation Steps:
- Click "Interface Permissions" button in operation column
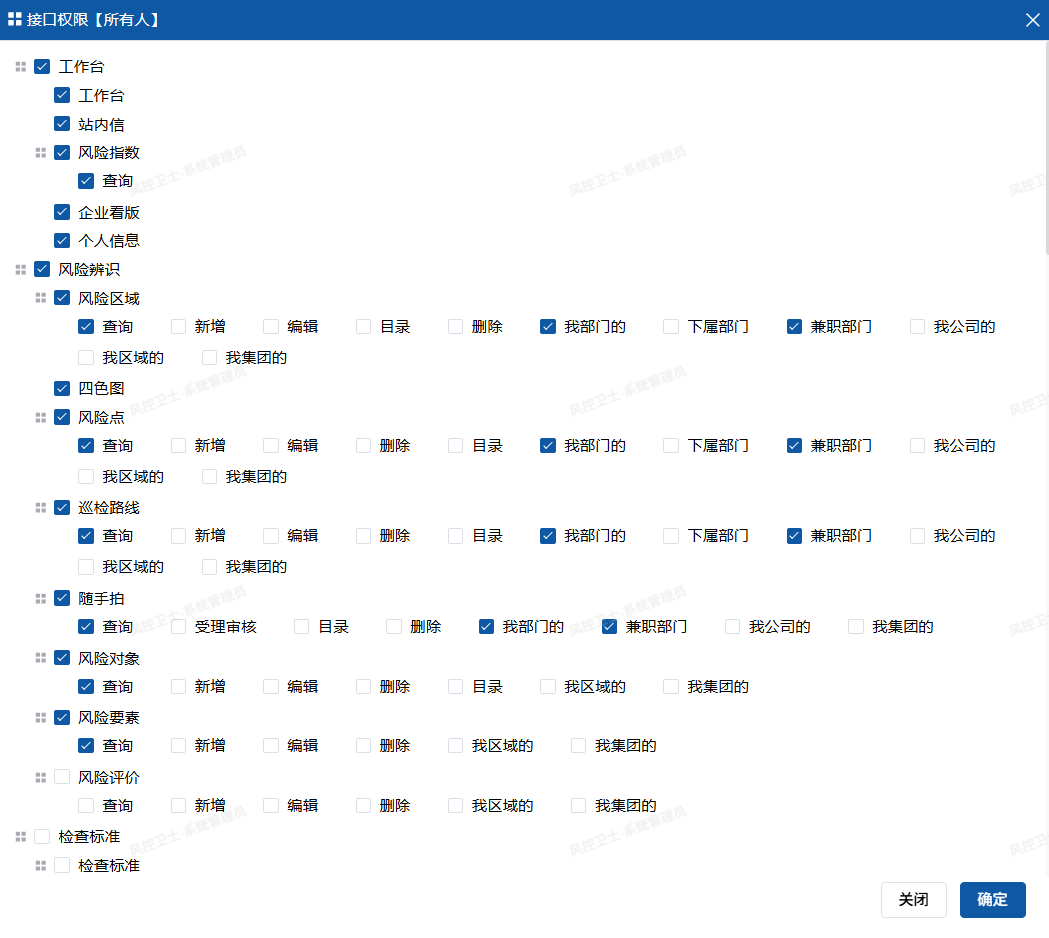
- Check functional permissions in the permission tree
- Click "Confirm" to save
Function Description:
- Define system functions accessible to the role
- Support module-level/operation-level permission control
5. Set Blacklist
Operation Steps:
- Click "Blacklist" button in operation column
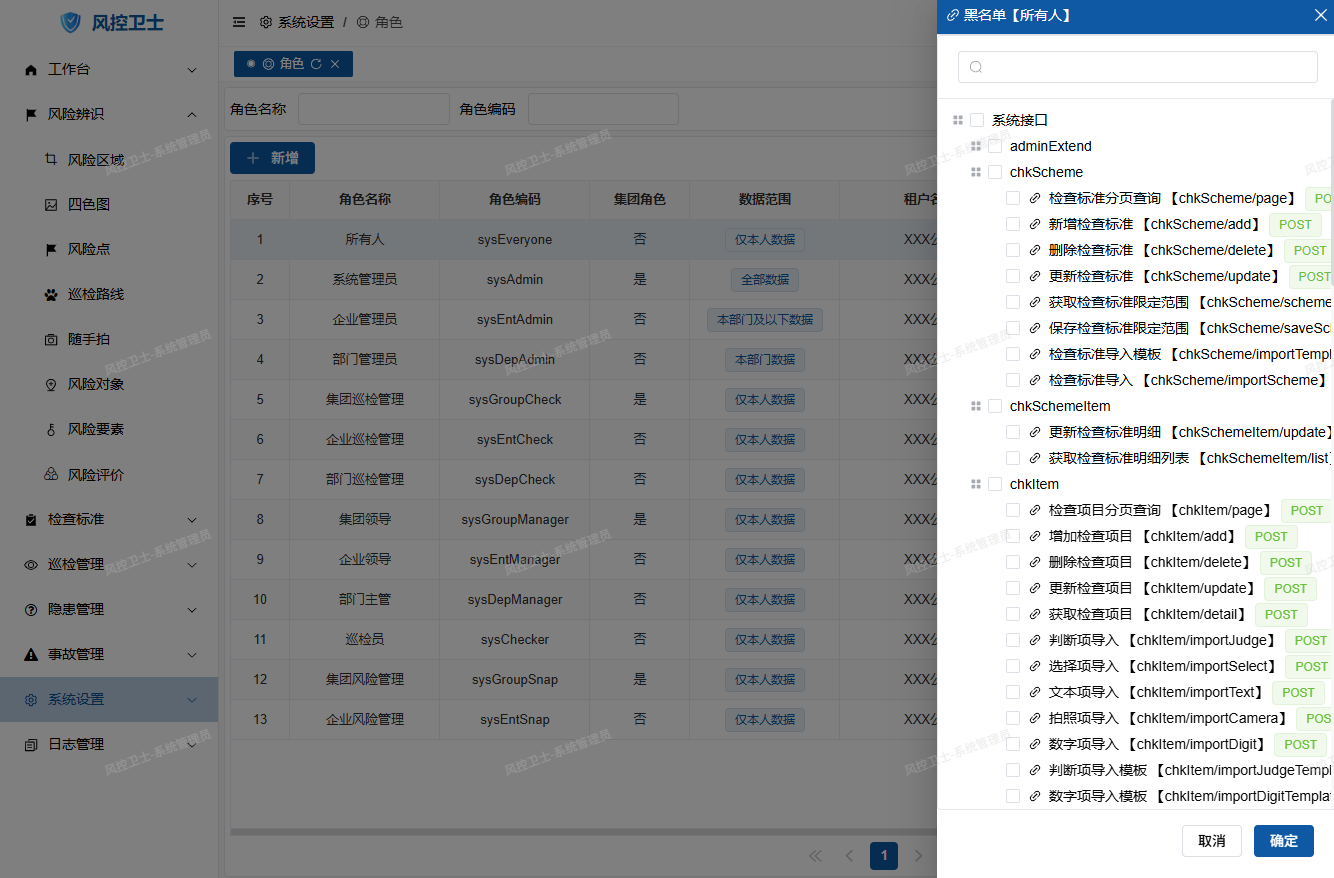
- Check prohibited API interfaces
- Click "Confirm" to save
Application Scenarios:
- Restrict sensitive operations (e.g. data export)
- Prevent unauthorized access
6. Define Data Scope
Operation Steps:
- Click "Data Scope" button in operation column
- Select visible scope:
- All Data: All system data
- Current Department and Below: Current department and sub-departments
- Current Department: Only current department data
- Personal Only: Personal related data
- Custom: Manually select department scope
- Click "Confirm" to save
III. Initial Role Description
1. System Administrator
- Permission Scope: Entire system
- Core Functions:
- Organization management
- Role permission design
- System parameter configuration
- Monitor overall system operation
- Group Application: Also serves as group administrator
2. Company Administrator
- Permission Scope: Current company
- Core Functions:
- Manage company department structure
- Configure business processes
- Manage user accounts
- Modify company-level templates
3. Department Administrator
- Permission Scope: Current department and sub-departments
- Precautions:
- Complex permission configuration
- Recommended to be handled by company administrator
4. Group Inspection Administrator
- Core Functions:
- Develop group inspection standards
- Plan risk point routes
- Monitor group-wide inspection data
5. Company Inspection Administrator
- Core Functions:
- Develop company inspection plans
- Configure inspection standards
- Monitor company inspection data
6. Department Inspection Administrator
- Precautions:
- Not recommended to set separately
- Managed uniformly by company inspection administrator
7. Group Risk Administrator
- Management Scope:
- Risk index
- Hazard management
- Incident records
- Risk factors
- Risk assessment
8. Company Risk Administrator
- Management Scope:
- Monitor company risk data
- Manage hazard resolution processes
- Maintain incident records
- Risk factors
- Risk assessment
9. Group Leadership
- Data Permission: View group-wide statistical analysis data
- Operation Restrictions: View-only permission
10. Company Leadership
- Data Permission: View company statistical analysis data
- Operation Restrictions: View-only permission
11. Department Manager
- Permission Characteristics:
- Manage department affairs
- Approve department workflows
- View department data
12. Inspector
- Core Functions:
- Execute on-site inspections
- Report hazards
- Complete inspection records
13. Everyone
- Essential Role: Must be assigned to every user
- Basic Permissions:
- Personal information management
- Notification viewing
- Basic operation permissions
IV. Best Practices
1. Role Planning Principles
- Least Privilege: Assign permissions as needed
- Separation of Duties: Split critical permissions
- Naming Conventions: Department + Function (e.g. "Finance_ExpenseApproval")
2. Permission Configuration Suggestions
- New Roles: Copy similar roles for modification
- Regular Review: Clean up invalid roles quarterly
- Test Verification: Create test accounts to verify permissions
3. Permission Change Management
- Change Records: Document reasons for permission adjustments
- Impact Assessment: Evaluate scope of permission changes
- User Notification: Notify users in advance of major changes
V. Precautions
- Initial Role Protection:
- Prohibit modifying initial role codes
- Permission adjustments require caution
- Permission Inheritance:
- Users inherit union permissions of all roles
- Blacklist permissions take precedence
- Deletion Impact:
- Deleting roles automatically disassociates users
- Historical operation records are preserved
